Anatomy of a Phishing Attack
At the most basic level, a phishing scam involves sending fraudulent emails that appear to be from a reputable company, with the goal of deceiving recipients into either clicking on a malicious link or downloading an infected attachment, usually to steal financial or confidential information.
Below is a guide to help you identify components of a phishing email. While steps are in place to prevent spam from being delivered to mailboxes, it is ultimately an individual's responsibility to remain vigilant when reading and responding to emails. If you are ever in question on the validity of an email you receive, please DO NOT download any attachments and forward the suspect email to spam@degnon.org.
Subject line
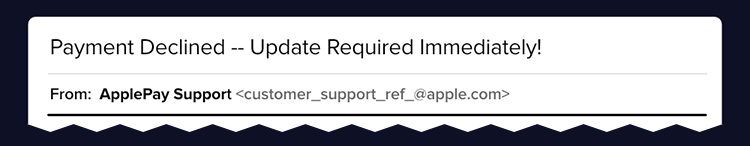
Phishing campaigns typically aim to create a sense of urgency using intense language and scare tactics, starting with the email’s subject line. Common themes among phishing emails are that something sensitive, such as a credit card number or an account, has been compromised. This is done to induce the recipient into responding quickly, without recognizing the signs of a scam.
“From” field
To work, phishing campaigns must trick the email recipient into believing that the message is from a reputable company. As such, the email will appear to come from a legitimate entity within a recognized company, such as customer support. Upon closer look, however, you can see that both the name of the sender and the sender’s email address is a spoof on a known brand, not a real vendor.

“To” field
Phishing emails are often impersonal, addressing the recipient as a “user” or “customer.” This is a red flag; while businesses may send out mass eblasts announcing a sale or service, legitimate companies will address you by name when asking for an update to financial information, or dealing with a similarly sensitive matter.
Body copy
As with the subject line, the body copy of a phishing email is typically employs urgent language designed to encourage the reader to act without thinking. Phishing emails are also often riddled with both grammar and punctuation mistakes.

Malicious link
A suspicious link is one of the main giveaways of a phishing email. These links are often shortened (through bit.ly or a similar service) or, as above, are formatted to look like a legitimate link that corresponds with the company and message of the fake email. However, rolling over the link shows a malicious address that doesn’t take you to the stated web address.
Scare tactics
In addition to urgent language, phishing emails often employ scare tactics in hopes that readers will click malicious links out of alarm or confusion. Such messaging is often framed around updates that are immediately required or payments that must be made within a certain amount of time.

Email sign-off
As with the email’s greeting, the sign-off is often impersonal — typically a generic customer service title, rather than a person’s name and corresponding contact information.
Footer
A phishing email’s footer often includes tell-tale signs of a fake, including an incorrect copyright date or a location that doesn’t correspond with that of the company.

Attachment(s)
In addition to malicious links, phishing scams often include malicious downloadable files, often compressed .zip files, which can infect your computer.
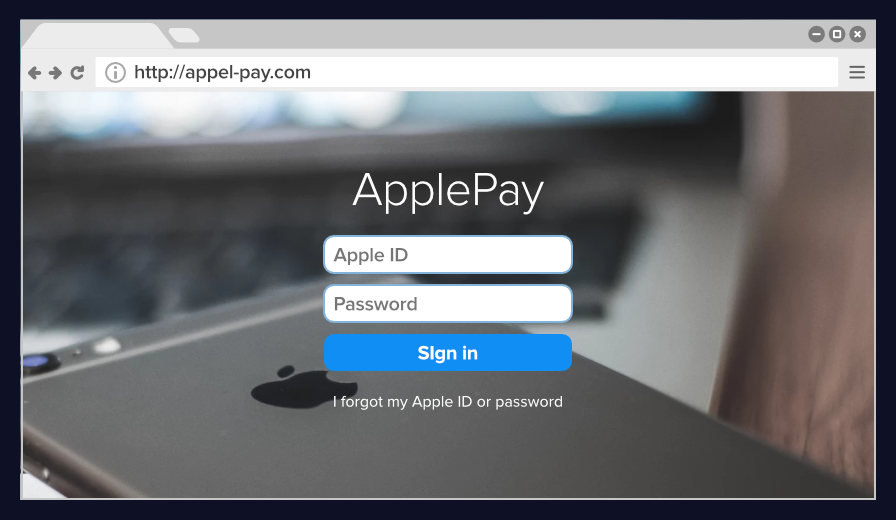
Malicious landing page
If you do click on a phishing link, you’ll often be taken to a malicious landing page, much like the one above. There are several ways to spot a malicious landing page:
- Website address: The web address of a malicious landing page attempts to mimic the web address of a legitimate company, but errors such as misspellings and unsecure connections denote an unsafe website.
- Missing navigation and footer: The goal of a malicious landing site is to take your information. As such, these pages are often bare-bones. Here, you can see that the landing page is missing both the header and footer of Apple’s ID sign-in page.
- Misspelling: Like in the phishing email, the malicious landing page will attempt to mimic a real company, but small oversights can tip you off: like above, where “Apple Pay” is misspelled as one word.
- Information collection: The goal of phishing scams is to get you to enter personal or financial information, so malicious landing pages will almost always include some type of information collection form that deviates slightly from the company’s legitimate landing page. In the malicious page above, users are required to enter their Apple ID password; this is not required on the actual Apple ID login page.
